You Don’t Have to Be a Cybersecurity Expert to Get MDR Security Expertise
Leverage Managed SOC Services for Advanced Threat Protection

Get a Free Trial Now
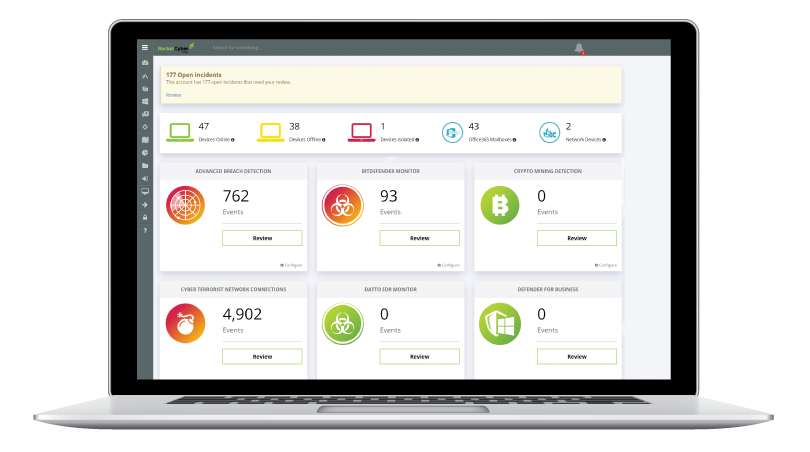
COMPREHENSIVE MANAGED DETECTION & RESPONSE

Endpoint Security
Protect your endpoints with Windows, MacOS, and Linux event log monitoring, advanced breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party next-gen AV integrations and more.

Network Security
Gain new levels of network protection with firewall and edge device log monitoring integrated with real time threat reputation, DNS information and malicious connection alerts.

Cloud Security
Secure the cloud with Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins and overall Secure Score.
24X7 MANAGED SOC POWERED BY CYBERSECURITY EXPERTS
Managed SOC is a managed detection and response service that leverages RocketCyber’s Threat Monitoring Platform to detect malicious and suspicious activity across three critical attack vectors: Endpoint, Network and Cloud. Our team of veterans hunt, triage and work with your team when actionable threats are discovered.
Continuous Monitoring
Around the clock protection with real-time advanced threat detection
Breach Detection
We catch sophisticated and advanced threats that bypass traditional AV and perimeter security solutions
Threat Hunting
An elite cybersecurity team proactively hunts for malicious activities so you can focus on other pressing matters
No Hardware Requirements
Patent-pending cloud-based technology eliminates the need for costly and complex on-premise hardware
KEY FEATURES

SIEMless Log Monitoring
Monitor, search, alert and report on endpoint, network and cloud threat vectors, including key log data from Windows, MacOS, Linux, firewalls, networked devices, Microsoft 365 & Azure AD – all without requiring a SIEM or SIEM hardware.

Intrusion Monitoring
Real-time monitoring of malicious and suspicious activity, identifying indicators such as connections to terrorist nations, unauthorized TCP/UDP services, backdoor connections to command and control servers, lateral movements and privilege escalation.

Threat Intelligence and Hunting
Real-time threat intelligence monitoring, connecting to premium intel feed partners gives our customers the largest global repository of threat indicators for our SOC analysts to hunt down attackers and find advanced threats.

Next-Generation Malware
Use your preferred malware prevention or leverage our command and control application for Microsoft Defender, backed up with a secondary line of defense using our malicious detection of files, tools, processes and more.

Breach Detection
Detect adversaries that evade traditional cyber defenses. We identify attacker tactics, techniques and procedures, aligning to MITRE ATT&CK. This allows our SOC analysts to detect indicators of compromise before damage is done.

PSA Ticketing
Our SOC analysts investigate each alert, triaging them to produce tickets for your PSA system, along with the remediation details so you can do more without having to hire additional staff.

The SOC team is absolutely amazing. I do not mind getting a call at three o'clock in the morning because a user has handed over their MFA credentials to someone in the Netherlands. We have mitigated two separate data breaches that could have been catastrophic and had them mitigated and shut down within minutes thanks to the RocketCyber Managed SOC. We can't express how great our experience has been with RocketCyber.
Be the Cybersecurity Expert
Start leveraging managed SOC services for advanced threat protection now.
