On-demand Threat Hunting
RocketCyber’s On-demand Threat Hunting enables MSPs to proactively query the endpoint for common hunt methods in order to detect malicious, suspicious or informational activities that have circumvented prevention tools. Whether you’ve received new threat intelligence from a 3rd party or need the power to search for artifacts after an incident, on-demand threat hunting simply put, enables you to know what you didn’t know near real-time.
Multi-tenant threat hunting is supported. This is the ability to perform one hunt query across all endpoints and customers you are managing. Proactive on-demand hunting gives you answers before security prevention vendors create a detection and uncover what slipped through defenses.
OS Support:
Windows Workstation 7, 8, 8.1, 10
Windows Server 2008, 2012, 2016, 2019

ON-DEMAND THREAT HUNTING
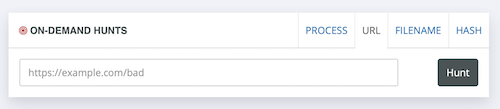
Performs threat queries on all of your customer endpoints searching for common hunts; Hashes, URLs, Processes and Files.
4 On-demand Investigative Queries
New to threat hunting? This is a great place to start. The free on-demand RocketApp provides you quick investigative capabilities to search for URLs, File Names, Hashes and Processes across all of your customer endpoints.
It’s very common adversaries leave behind malicious files and processes running. While there are many use cases for service providers and security operation centers, this RocketApp was developed to expose frequent endpoint investigations.
For advanced capabilities, detection methodologies and automation, explore the related RocketApp – Threat Hunting.