Threat Hunting
This RocketApp enables MSPs to perform threat hunting on Windows and macOS endpoints. We define hunting as the process of investigating the endpoint to detect threats that evade traditional security defenses such as firewalls and anti-virus. Threat hunting is gaining momentum with managed service providers, delivering strong benefits such as improved detection of APTs, reduced investigation time, in addition to expediting detection and response.
With RocketCyber’s threat hunting, you can:
- Detect if endpoints are compromised across the fleet of your managed customers.
- Add threat intelligence feeds to deliver continous threat monitoring.
- Generate threat tickets to your PSA system (ConnectWise / Autotask).
OS Support:
Windows Workstation 7, 8, 8.1, 10
Windows Server 2008, 2012, 2016, 2019
macOS Mojave 10.14, Catalina 10.15

THREAT HUNTING
Provides investigative capabilities to find malicious activity through 17 categories of analysis, e.g. processes, hashes, URLs, and IOCs.
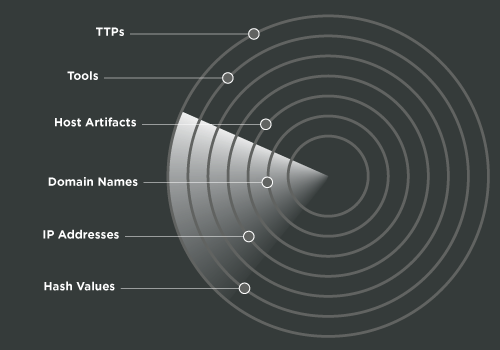
Hunting the Compromise
How many days do attackers who breached defenses dwell inside your customer networks before they are detected? Proactive hunting reduces the dwell time and with RocketCyber, you can detect hashes and ip address indicators in its most simplest form to the most challenging tactics, techniques and procedures (TTPs).
Methodologies include 17 different configurable options such as hunting for DNS Cache Entries, Windows Events, Network Connections, Services, Registry Keys and more. Hunters can also upload YARA indicator of compromise rules.
Multi-tenant hunting is a benefit for MSPs who are offering cyber services to multiple customers. This refers to creating a manual and/or automated hunt and applying it across all customer endpoints that are being managed.