Business Email Compromise – FBI Remediation Guidance
Cyber Criminal Cost US Businesses $2 Billion
On April 6, 2020, the FBI issued Alert # I-040620-PSA, announcing that cyber criminals conduct business email compromises through exploitation of cloud-based email systems, costing US businesses more than $2 billion.They include 11 different bullets suggesting remediation actions from multi-factor authentication, disable mail forwarding, prohibit legacy email protocols i.e. POP, IMAP, and SMTP to foreign login suspicious activity monitoring. Historically, many small-medium businesses (SMB) have been reluctant to take action on such remedial advice, until they’ve fallen victim to a business email compromise (BEC).
While many SMB owners have undermined such protection, the negligence is partially contributed to the inconvenience of authenticating and the other factor tied to technology costs. Ironically, most SMBs indicate that one of their top concerns is email security.
Many business owners are better convinced and educated with a visual. Let’s break down four of the suggested FBI recommended actions by providing five evidence examples when the protection is not in place and/or evaded.
1. Legacy Email Protocols
Most commonly configured for convenience and often detected where employees-on-the-go communicate with a local email client, such as Microsoft Outlook.
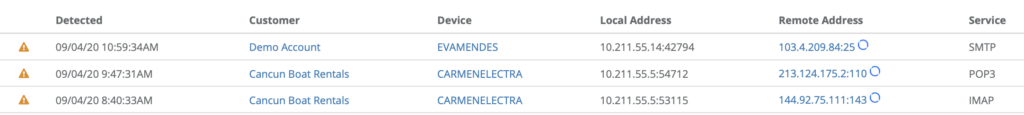
Figure 1 – Legacy Protocols
SMTP, POP3, IMAP
The concern: legacy protocols can evade authentication policies, messaging is unencrypted (clear-text) and prone to email sniffing, vulnerable to exploitation, easier for spammers / phishers to relay unsolicited email posing as the user and many more.
2. Suspicious Login Activity
Regardless of the origin, foreign or not, the risk is real and yes even outside of Russia and China. In North America alone, Microsoft 365 is by far the adopted cloud-based email of choice.
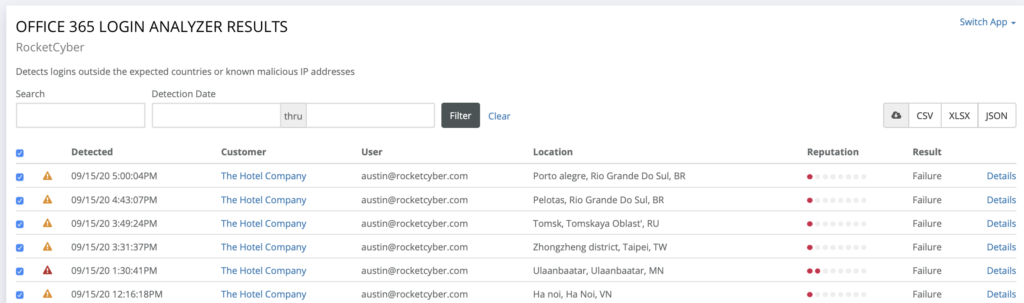
Figure 2 – Office 365 Bruteforce Failed Login Activity
The repetitive process of trial-and-error to guessing login information
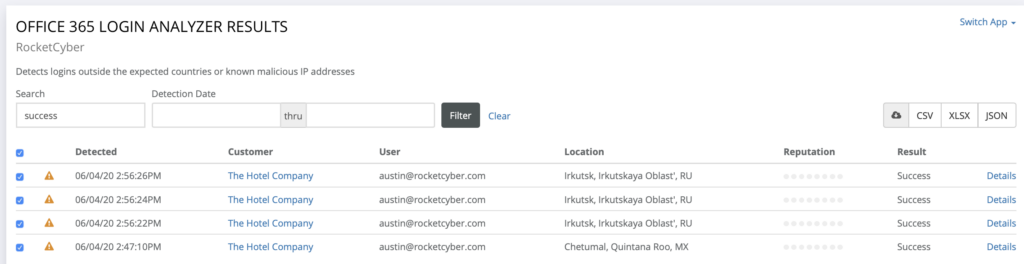
Figure 3 – Successful Authentication Login Activity
Residing in two demographic regions during a short time span is one potential indicator of a Business Email Compromise.
The concern: With the mass adoption of Microsoft 365 who wouldn’t be concerned about unauthorized access to their email system. Adversaries are continuously seeking a foothold with minimal layers of protection. This is one of the biggest blind spots in the industry – lack of suspicious login activity monitoring resulting in existing email compromises whereby the attacker remains unnoticed for a significant period of time.
3. Unauthorized Email Forwarding
Simply put, the copying of inbound and outbound email data to an illicit external account.
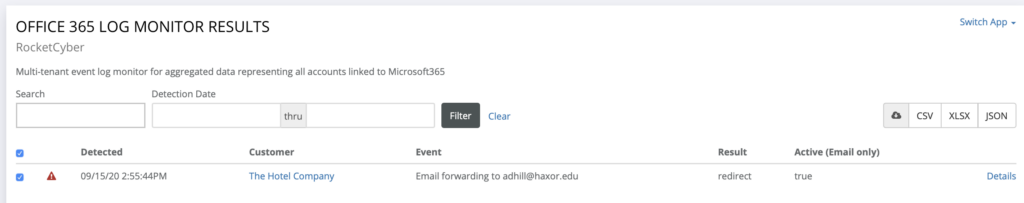
Figure 4 – Unauthorized Email Forwarding
Active Rule to External Domain
The concern: While mail forwarding has its legit usage, it is quite common for confidential data to be forwarded by the adversary or rules intentionally and unethically created by a disgruntled employee with the sole purpose of syphoning corporate information.
4. Multifactor Authentication
Kudos to the business for implementing a corporate policy by adding a layer of login authentication security. Is the policy configured properly and does the employee have rights to disable/circumvent the control?
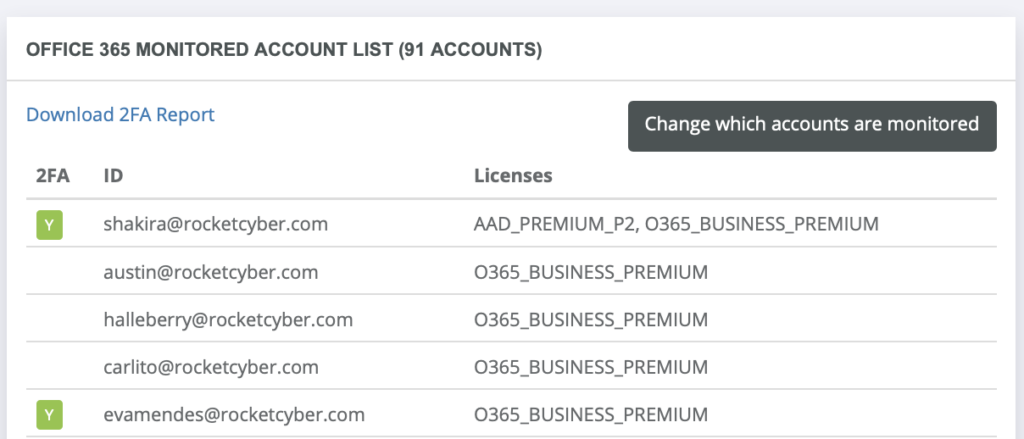
Figure 5 – 2FA (two-factor authentication)
Identify what employees are adhering to the 2FA policy
The concern: Without 2FA, the likelihood of email compromise is higher and prone to password guessing attacks and stolen credential unauthorized logins.
Microsoft 365 Common Challenges for MSPs
Beyond and above the FBI recommendations for protecting Microsoft 365 environments, the RocketCyber SOC team made it our mission to solve common challenges we repeatedly hear from MSPs related to Office 365 security monitoring:
- Lack of Multitenancy Insight – Single centralized console to query, report and investigate threat data across an MSP’s fleet of customers and 365 users.
- Shortage of IT / Security Staff – Who is going to monitor, detect and respond to 365 threat data given the shortage of cyber skillsets in the industry?
- Integration with MSP Operations – When threats, configurations and 365 issues do surface, what is the workflow process of responding to tickets with current PSA investments, i.e. ConnectWise & Autotask?
Our response to the challenges: RocketCyber’s SOC platform, delivered as a service was built and architectured for MSPs delivering cyber services to SMBs. This spans a highly scalable multitenant architecture, integrates with popular RMM, PSA and other existing technology stack investments, consolidating all of the threat telemetry and leveraging experienced security veterans eliminating the burden of hiring internal security staff around the clock.
Conclusion
Business email compromise is a type of fraud that is detrimental to any employee and/or business experiencing such an incident. While the list of FBI remedies all merit consideration, it’s not practical for most SMBs to adopt each line item, but yet should serve as list of controls for improving the overall email security hygiene of the business. Figures 1-5 are screen captures by the RocketCyber Managed SOC demonstrating visibility and insight combating cyber-criminal business email activity.
To learn more about RocketCyber’s 24/7 Managed SOC – Business Email Compromise monitoring capabilities across your fleet of Microsoft 365 users, schedule an online demo with a RocketCyber security engineer today.
